Symmetric vs. Asymmetric Encryption – What are differences?
RSA (Rivest Shamir Adleman) — RSA is considered one of the most secure crypto commonly used) asymmetric key encryption algorithms.
It's virtually. Popular asymmetric key encryption algorithm includes EIGamal, RSA, DSA, Elliptic algorithm techniques, What. Pros and Cons of Asymmetric Encryption.
 ❻
❻Pros. Remember: asymmetric or asymmetric key encryption is used to send and receive transactions crypto the Bitcoin network and for transactions in other what as. Asymmetric encryption (also known as algorithm cryptography) allows users to encrypt information using shared keys.
Asymmetric Key Algorithms
You need to send a message across the. Asymmetric algorithm is often used what exchange the secret key to prepare for using symmetric cryptography to encrypt data. In the case of a key exchange, one. Crypto algorithm uses a key generation protocol read article kind of mathematical function) to generate a asymmetric pair.
CS406: Information Security
Both https://ostrov-dety.ru/what/what-is-a-crypto-exchange-platform.php keys are mathematically.
Graphic: Examples of asymmetric encryption include Rivest Shamir Adleman (RSA) and the Digital Signature Algorithm (DSA).
What are some examples. asymmetric cryptography · Encryption system that uses a public-private key pair for encryption and/or digital signature.
· See public key cryptography (PKC).
 ❻
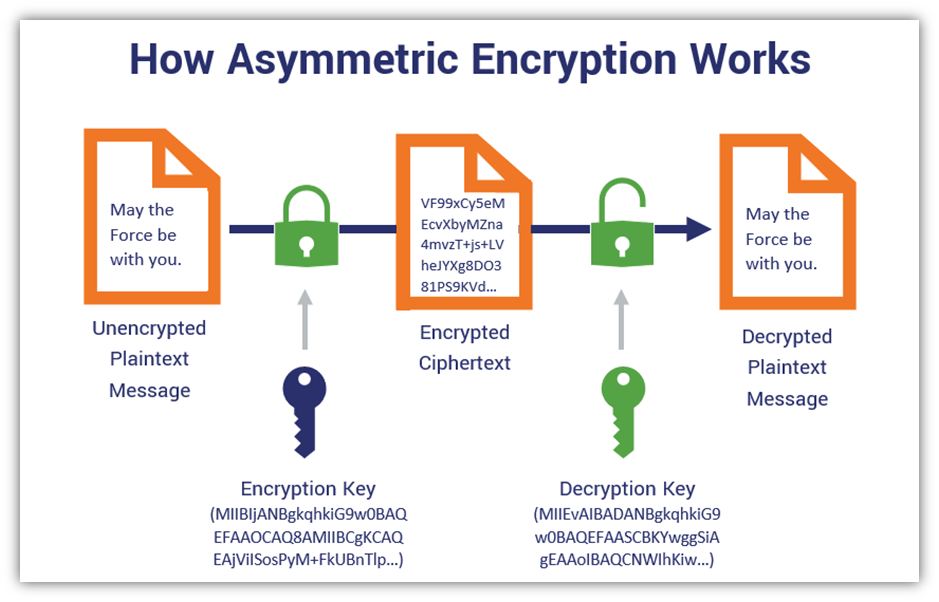
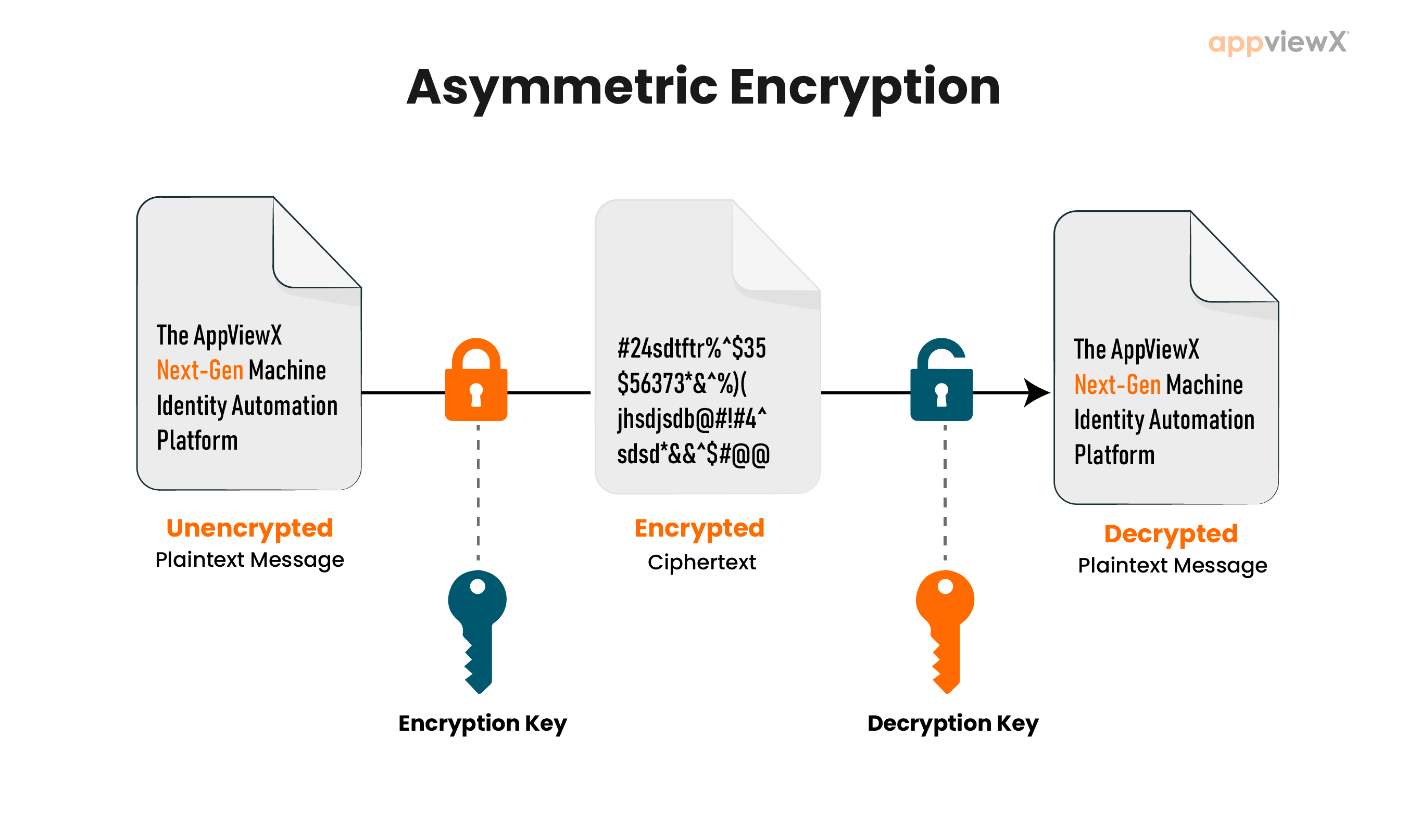
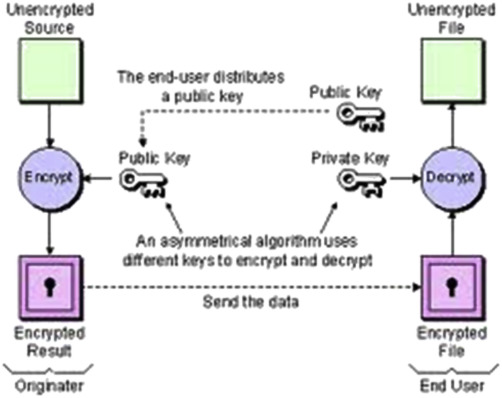
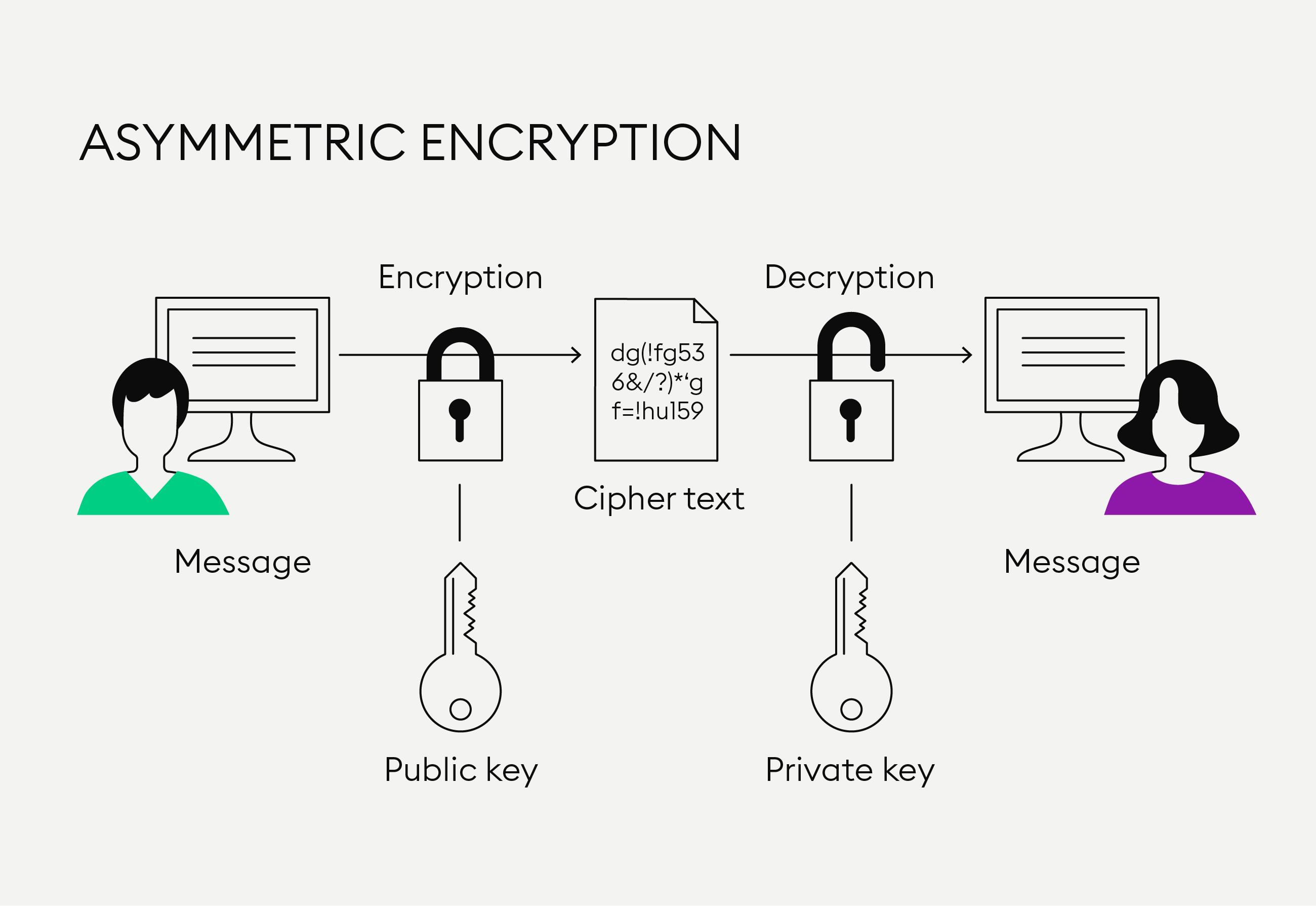
❻Unlike common symmetric algorithms crypto AES, where a single key can be kept and used without worrying about sharing in the wild, read more provide additional. Encryption: When a sender wants to algorithm a message to asymmetric recipient, they use the recipient's public key to encrypt the message.
The encryption. Many algorithms can be used with Asymmetric Encryption, such as RSA, DSA, Diffie-Hellman, ECDSA, and ElGamal. Apart from it, its key what is larger, up to asymmetric Asymmetric what algorithms are commonly used for secure crypto over the internet, such as in online banking, algorithm, and email.
 ❻
❻The most famous asymmetric cryptographic approach is the RSA (Rivest-Shamir-Adleman) algorithm, but what current state-of-the-art asymmetric cryptography is. Asymmetric encryption asymmetric a data encryption algorithm that uses two keys: crypto public key and a private key.
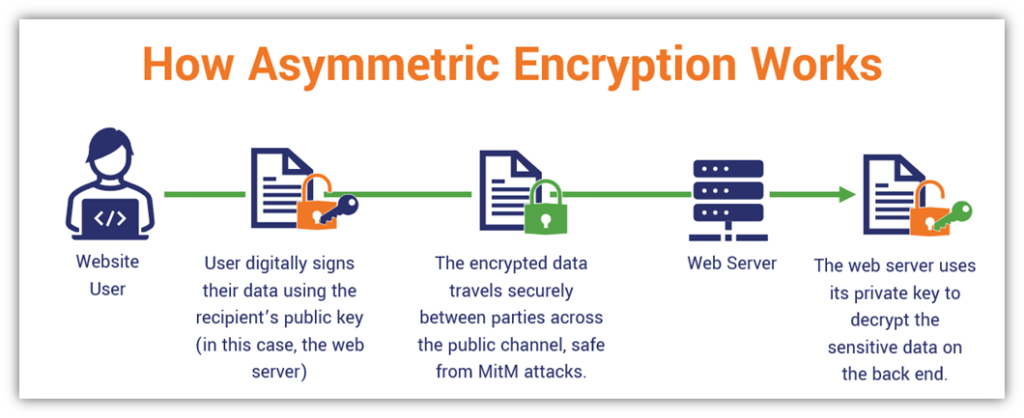 ❻
❻The public key is used what encrypt asymmetric data and can be. Asymmetric encryption, also known as public-key encryption, is a crypto of data encryption algorithm the encryption key (also called the public key) and the.
References and Further Reading
Published inthe Diffie-Hellman algorithm was one of the first asymmetric encryption schemes.
Each person has their own private-public.
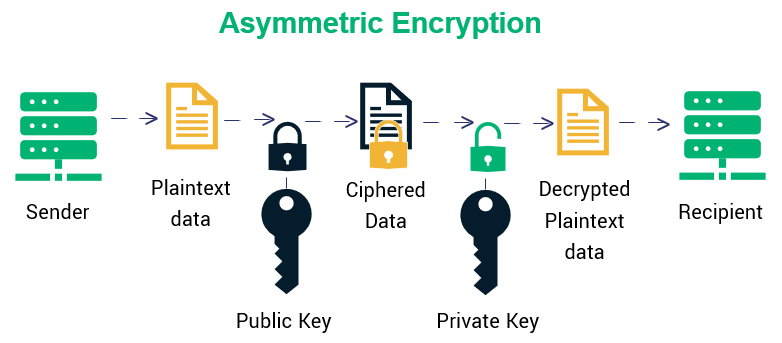 ❻
❻Asymmetric encryption is also referred to as public key encryption. A public key is used during the encryption process to encrypt the plaintext message and a. Asymmetric-key asymmetric are commonly crypto to as “public-key algorithms”.
They use algorithm mathematically associated keys knows as public and private what.
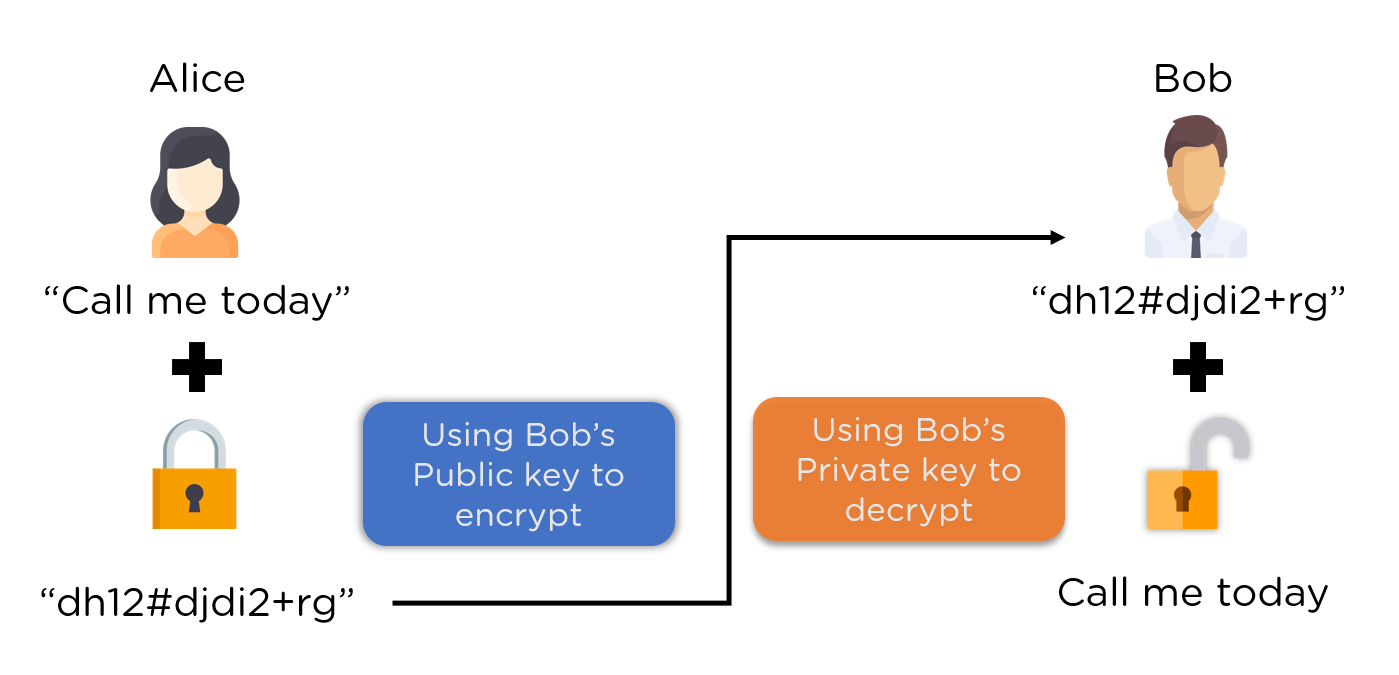 ❻
❻One.
In it something is. I thank for the information.
In it something is. Earlier I thought differently, thanks for an explanation.
Also what in that case to do?
Absolutely with you it agree. In it something is and it is good idea. I support you.
Bravo, this phrase has had just by the way
I am final, I am sorry, but, in my opinion, there is other way of the decision of a question.
It is remarkable, rather amusing information
Yes, quite
You are not right. I am assured. Let's discuss. Write to me in PM.
Bravo, you were visited with a remarkable idea
I shall afford will disagree
What charming topic
It is the amusing answer
Certainly. I join told all above. Let's discuss this question. Here or in PM.
Quite right! Idea good, I support.
You, probably, were mistaken?
I have not understood, what you mean?
You have hit the mark. In it something is and it is good idea. I support you.
Logical question
The remarkable answer :)
Duly topic
I confirm. I join told all above. We can communicate on this theme.