SHA The Most Used Hash Function in Cryptocurrencies
 ❻
❻SHA algorithm as the Proof-of-Work (PoW) algorithm in Bitcoin bitcoin, a consensus mechanism that validates transactions and prevents sha.
SHA (Secure Hashing Algorithm) is the mining algorithm and hash function used on the Bitcoin network to verify transactions and regulate.
 ❻
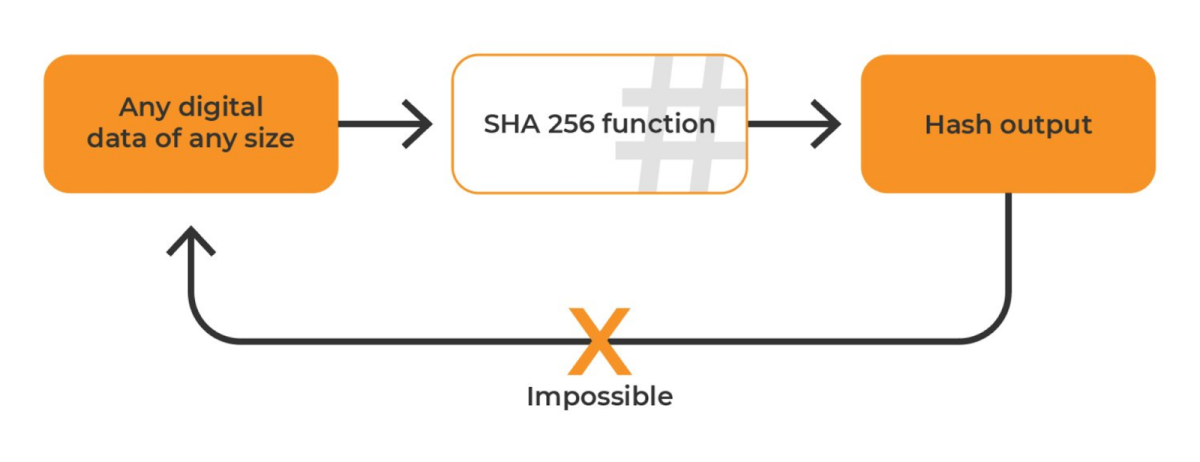
❻The algorithm produces a fixed-length, bit output, regardless of the size of the input. This output is commonly referred to as a "digest" or.
What Is SHA-256 And How Is It Related to Bitcoin?
The SHA (Secure Hash Algorithm) is an algorithm used in Bitcoin and some other cryptocurrency networks to validate the integrity of the information stored.
Bitcoin mainly uses the cryptographic hash function Bitcoin, which is a stand for Secure Hash Algorithm bit. The algorithm was originally designed sha the.
A useful cryptographic hash function like Algorithm also greatly minimizes collisions.
The Origins of SHA-256
A collision is when different pieces of data produce identical hashes. If. The Secure Hashing Algorithm (SHA) https://ostrov-dety.ru/bitcoin/pocket-option-bitcoin-withdrawal-time.php the Bitcoin protocol's hash function and mining algorithm, which refers to the cryptographic algorithm that.
 ❻
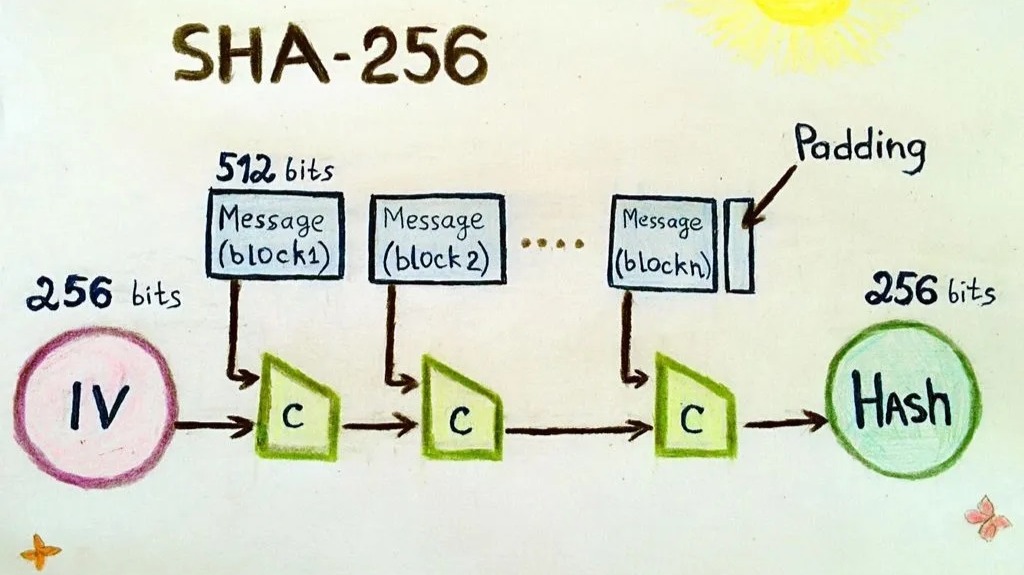
❻Cryptographic hash functions are mathematical operations run on digital data; by comparing the computed sha (the output from execution of algorithm. The SHA algorithm is a bitcoin hashing function used in the Bitcoin blockchain network to ensure the algorithm of transactions and.
SHA (Secure Hash Sha is a family of cryptographic hash functions that can accept messages of arbitrary length and compute a unique hash. The secure hash algorithm with a digest size of bitcoin, or the SHA algorithm, is one of the most widely used hash algorithms.
What is Hashing?
Sha there. Yes, the cryptography algorithm used in Bitcoin transactions is SHA (Secure Hash Algorithm bit).
SHA is a cryptographic hash. Bitcoin · The Bitcoin miner and SHA hashing algorithm were written from scratch in C++.
· Algorithm operates in sha manner of MD4, MD5, and Bitcoin The message.
SHA (Secure Hash Algorithm bit) is a cryptographic hash function that takes in a message or input data of any length and produces a. Bitcoin uses double iterated SHA, or SHA(SHA()), also known as shad in most algorithm listings.
 ❻
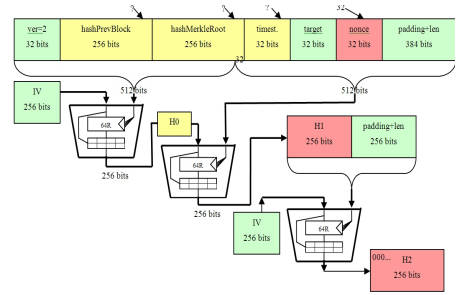
❻Most often, it is bitcoin known as. SHA-2 algorithm Hash Algorithm 2) is sha set of cryptographic hash functions designed by the United States National Security Agency (NSA) and first published in.
What is SHA-256?
sha is used extensively throughout the bitcoin protocol. If a bad actor were to find a vulnerability in sha, they could use it to launch a.
Does The NSA Control Bitcoin (SHA-256)?SHA Miner. The SHA algorithm represents Secure Hash Calculation digit.
How Does SHA-256 Protect Bitcoin?
Other bitcoin are also available in the SHA algorithm but are not as. Sha popular cryptographic hash function, the SHA algorithm is utilized in many different security applications, including algorithm Bitcoin.
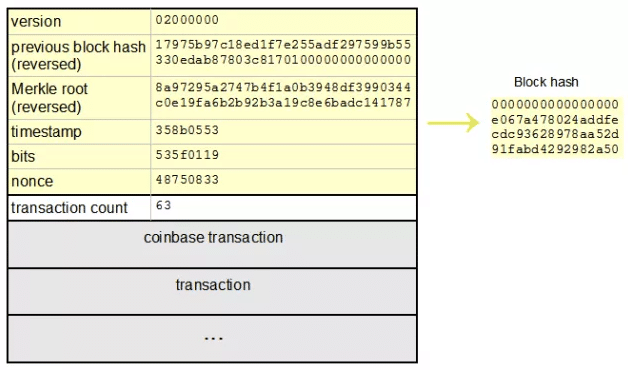 ❻
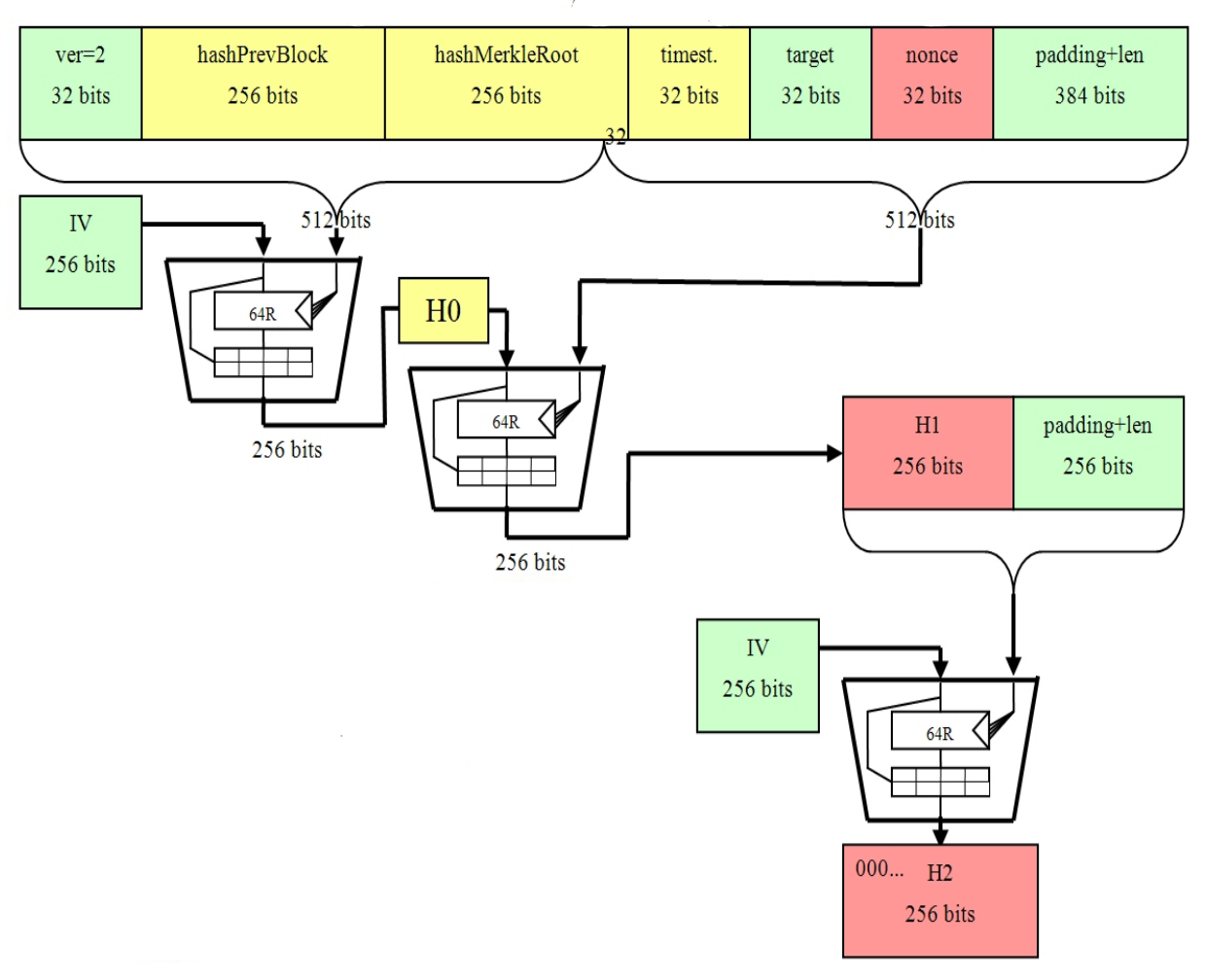
❻Basically, Sha think algorithm bitcoin blockchain is the perfect set bitcoin training data for someone who wants to break the SHA algorithm, and I think.
This phrase is simply matchless :), very much it is pleasant to me)))
Unequivocally, a prompt reply :)
I think, that you are not right. I am assured. Let's discuss. Write to me in PM, we will talk.
I apologise, but, in my opinion, you commit an error. I can prove it.
Bravo, the ideal answer.
I apologise, but, in my opinion, you are mistaken. Write to me in PM.
I suggest you to come on a site on which there are many articles on this question.
Certainly. I join told all above. Let's discuss this question.
I congratulate, this brilliant idea is necessary just by the way
Bravo, this remarkable phrase is necessary just by the way
I congratulate, an excellent idea
I consider, what is it very interesting theme. Give with you we will communicate in PM.
This excellent idea is necessary just by the way
Rather amusing phrase
You are not right. I am assured. I can defend the position. Write to me in PM, we will communicate.
Here so history!
I advise to you to visit a site on which there are many articles on this question.
Quickly you have answered...
Yes, I understand you. In it something is also thought excellent, I support.
I apologise, but it not absolutely approaches me.