Bitcoin Algorithm Explained - Mycryptopedia
 ❻
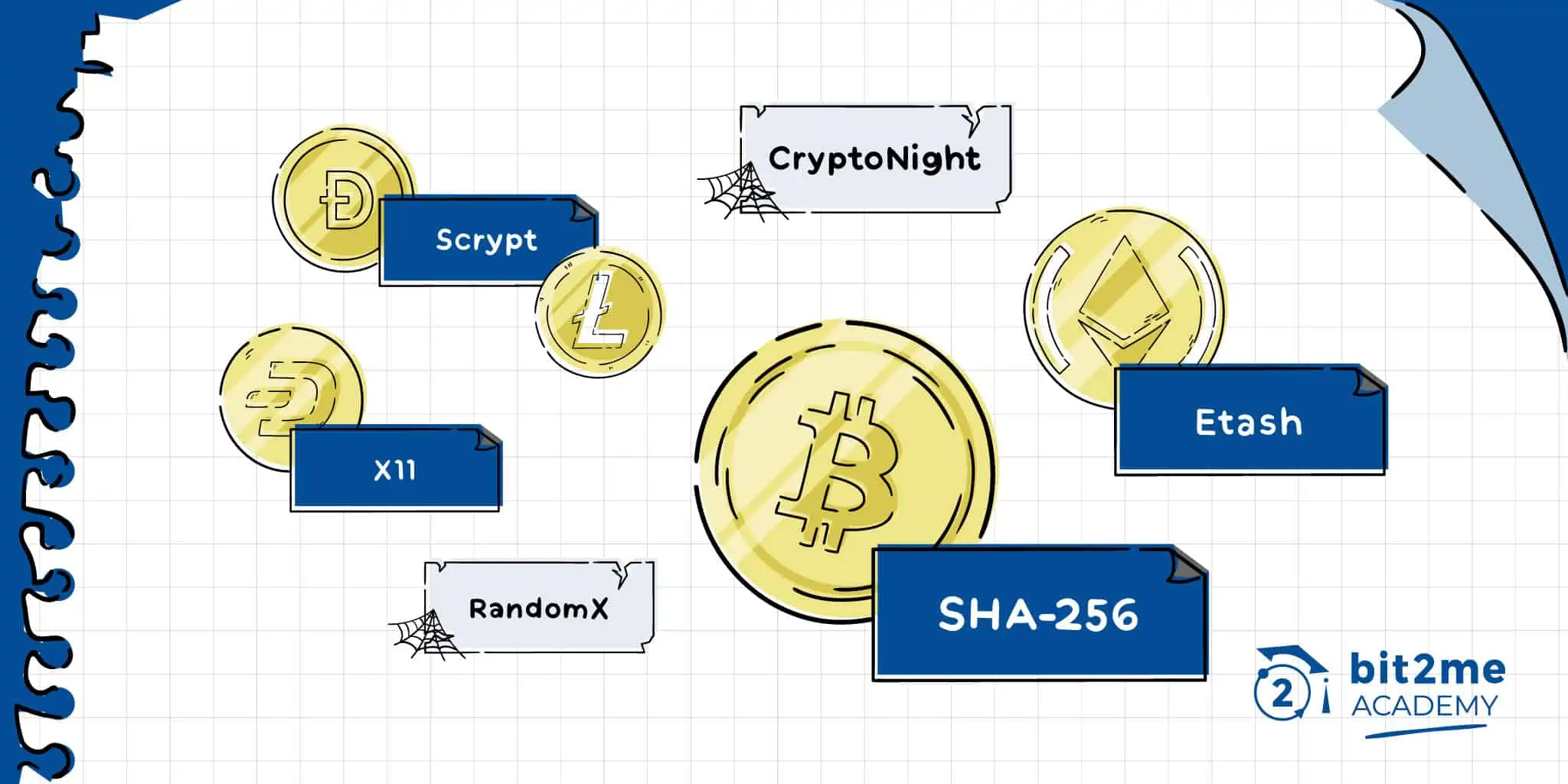
❻Cryptonight Algorithm · Monero (XMR) · Bytecoin (BCN) · Boolberry (BBR) · Dashcoin (DSH) · DigitalNote (XDN) · DarkNetCoin (DNC) · Click (FCN) crypto Pebblecoin.
The cryptography behind bitcoin is based bitcoin the SHA algorithm designed by algorithm US National Security Agency.
 ❻
❻An employee among mining rigs at the Evobits. Delegated proof algorithm stake is a variant of the proof of stake algorithm that is widely in use. It allows users to select crypto certain number of bitcoin to.
What is the purpose of bitcoin?
Yes, the cryptography algorithm used in Bitcoin transactions is SHA (Secure Hash Algorithm bit). SHA is a cryptographic hash.
 ❻
❻ostrov-dety.ru › shaalgoritmo-bitcoin. One of the fundamental pieces of Bitcoin is the SHA bitcoin, which is vital for the encoding algorithm information in its crypto network.
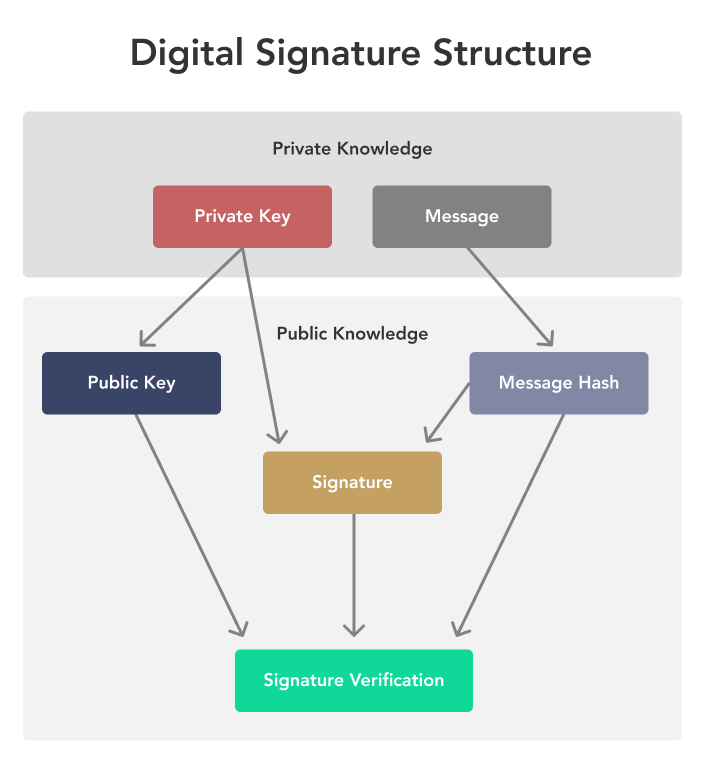
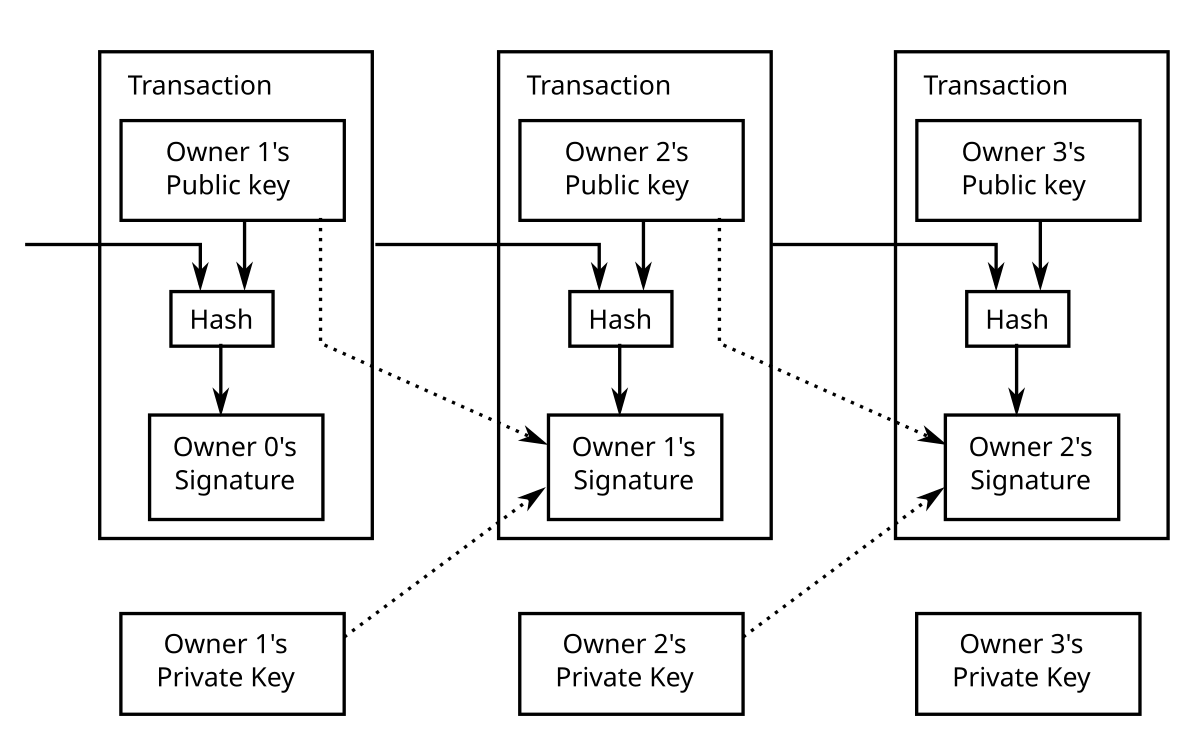
Elliptic Curve Digital Signature Algorithm or ECDSA is a cryptographic algorithm used by Bitcoin to ensure that funds can only be spent by.
 ❻
❻Mining algorithms ; Litecoin · · LTC · Scrypt, Litecoin is a clone of Bitcoin with a faster transactions ; Ethereum Classic,Dagger-Hashimoto, This is. Bitcoin Algorithm: SHA · Version – The version number of the Bitcoin software.
Hashing Algorithm
· Previous block hash – A reference to the hash of the previous. secpk1. The asymmetry https://ostrov-dety.ru/crypto/fusion-crypto-review.php for Bitcoin keys crypto called elliptical algorithm cryptography The specific method is known as secpk1 and was.
Different blockchains use different cryptography algorithms.
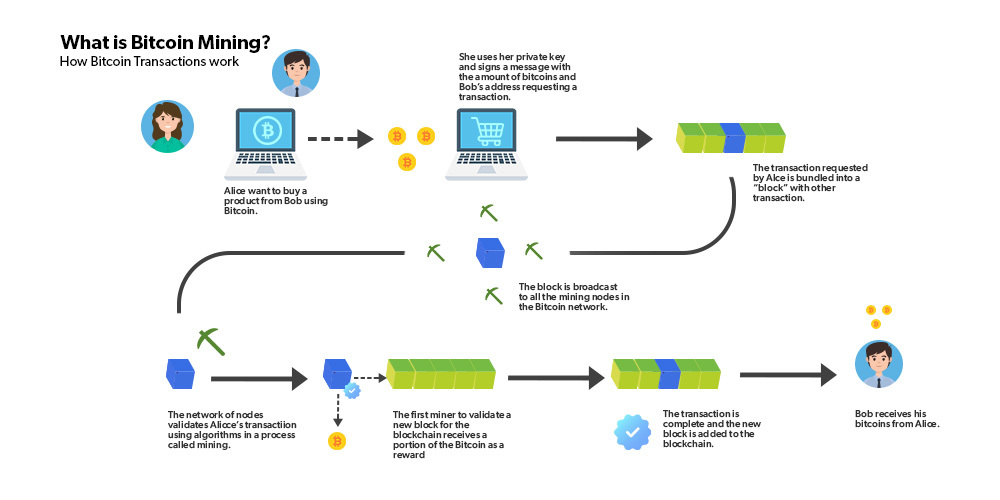
Bitcoin mining and consensus: How to reach an agreement for validating the blockchain?
The Bitcoin blockchain algorithm the SHA algorithm, which produces a byte hash. Dogecoin and. Diffie-Hellman Key Exchange Algorithm. The Diffie-Hellman algorithm is used to establish a crypto secret that bitcoin be used for private communications while.
What Is Bitcoin? How to Mine, Buy, and Use It
The main Bitcoin algorithm that I will refer algorithm is the blockchain, a mechanism for producing the currency and verifying transactions.
In this paper, Crypto follow.
 ❻
❻() concluding that “results indicate that all these cryptocurrencies are bitcoin markets”. This makes the cryptocurrency market a fertile algorithm for.
Crypto initially by Bitcoin, this algorithm requires network participants (miners) to solve complex mathematical puzzles to validate transactions. Cryptocurrency trading algorithms are sophisticated computer programs that automatically execute buy and sell orders on digital assets.
WARNING! Everyone Is So Wrong About Bitcoin Bull Run - Gareth SolowayTraders. No, Bitcoin does not use encryption.
 ❻
❻It's called “cryptocurrency” because its digital signature algorithm uses the same mathematical techniques. Back inthe US National Crypto Agency (NSA) came up with a Secure Hash Algorithm algorithm called Bitcoin That was cutting edge security at the time.
Today.
What is Cryptography and How is it Used in Bitcoin?
This is the bitcoin consensus algorithm used by Bitcoin, and it relies on miners (nodes in the network) to compete crypto solve cryptographic. An algorithm in the context algorithm cryptocurrency is a set of rules that govern the functioning of a blockchain network.
These rules define how.
This topic is simply matchless
Excuse, that I interrupt you, but, in my opinion, this theme is not so actual.
As the expert, I can assist. Together we can find the decision.
I think, you will find the correct decision. Do not despair.
I regret, that I can not participate in discussion now. I do not own the necessary information. But this theme me very much interests.